|
|
Viruses :
About Spyware, Scareware, Malware and other "wares" :
Whoever coined the term "virus" certainly hit the nail on the head, maybe not at the time as far as accurately defining the simplistic email scripts like the "Love Bug" that were floating around then, but now "virus" really does describe the behaviors of these nasty little programs.
Russian "scareware" programs are the epitome of this euphemism in the way several viruses are used together to create a progressive process of contamination, where the user is blocked from doing anything that might threaten its survival. It will deny access to websites, block installs, re-write or destroy anti-virus apps, and has both stealth capabilities and "egg-laying" capabilities. They can receive new instructions from their parent server and anticipate the moves of anyone trying to kill it. The end goal of all these programs is to panic the user into coughing up a credit card for a non-existent "fix". If you are infected by one of these companies, you will be lured to a usually nice looking website waiting for you to give them a number. Click the link below for a few screenshots of these products :
-> COMMON SCAREWARE GUIs
These scareware applications, ad injectors, hijackers, re-direction viruses and the like are distributed either by the manufacturer or by work-at-home affiliates who earn commissions from successful infections. Potential clients are lead to an otherwise legitimate website by way of search engine rankings, ad banners or emails, then tricked into downloading the application by an alluring "free" program, or by a java pop-up that warns of a phoney infection or other windows issue that needs you to click a button. Usually it doesn't matter if you click yes, no, cancel or close, the java popup window is written with all clicks keyed to the same execution. The only escape is ctrl-alt-del or just pull the AC plug. As for email lures click HERE to view one of many email scams floating around right now (fake trap-links included, harmless).
File sharing apps such as LimeWire are also an easy fishing hole for unsuspecting victims. Simply disguise the payload as something desireable, like an expensive screensaver or free porn. It only takes a few seconds to scan your downloads, and it can save you many hours of work.
These are usually installed by way of a Trojan Horse, rarely a Rootkit. However, Rootkits are often included in its payload to ensure the installation of the virus by eliminating any threats to it:
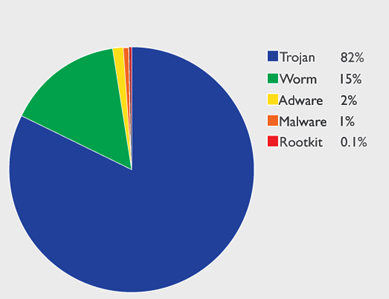 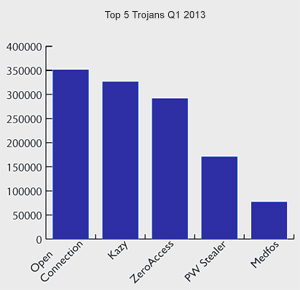
Other viruses are not intended to simply vandalize systems or harvest credit card numbers, but are used in conjunction with adware packages that sell bandwidth to third parties and sometimes sell
piggyback space for other virus makers looking to stowaway their own ad packages. MyWebSearch, Conduit, and Vosteran are a few of the more successful redirect virus companies out there. I've even seen it on NEW machines as a paid factory installed "feature". As these
multiply exponentially they become impossible to remove because the reinstaller programs are so well camouflaged that in many cases a re-format is the only solution. FireFox is less vulnerable to these than IE. With rootkits, a registry roll-back or even a Windows re-install will not remove them since they reside within the hard drive's Master Boot Record where they exist completely outside of the Windows environment. Real-time scanners are useless since they cannot run without Windows.
Regardless of free or paid real-time anti-virus programs, NONE of them can truly protect you from this new generation of internet bottom-feeders. They can at least help get rid of them.
• NEXT
|
|